Understanding the Ongoing Threat of Spyware: Intellexa’s Operations and Their Impact
In today’s digital age, cybersecurity remains a hot topic, with new threats emerging regularly. Recently, a joint investigation by Haaretz, Inside Story, and WAV Research Collective revealed that Intellexa, an Israeli spyware firm, is still operational and continues to exploit vulnerabilities, even in light of U.S. sanctions. The revelations are concerning, especially with reports of its spyware being used in countries like Pakistan.
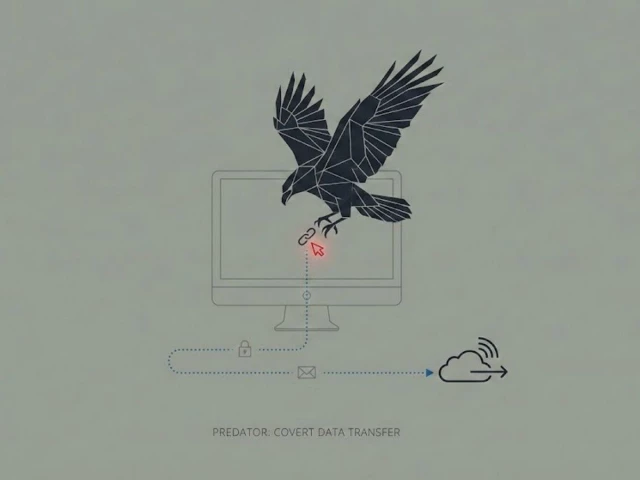
Intellexa’s flagship product, Predator, is a one-click spyware tool designed to covertly infiltrate devices and harvest sensitive data, including messages, photos, and other personal information. What’s more alarming is the discovery that Intellexa has maintained access to its clients’ surveillance operations despite past sanctions by the U.S. Treasury Department. This raises significant questions about accountability within the sphere of private surveillance firms.
The Alarming Rise of Aladdin
Adding to these concerns is the development of a new infection method called "Aladdin." This zero-click exploit utilizes malicious online advertisements to infect devices, meaning that users can become victims simply by viewing an ad. This stealthy approach makes it increasingly difficult to detect and defend against such spyware. It underscores the necessity for individuals and organizations alike to adopt stronger cybersecurity measures.
Predator’s Footprint in Pakistan
The report highlights a troubling case in Pakistan, where a human rights lawyer received a suspicious WhatsApp link, which has since been linked to Intellexa’s spyware. This incident marks a significant milestone, as it is the first confirmed use of Predator spyware in the country. A senior Pakistani intelligence officer has dismissed these claims as “baseless,” arguing that the allegations are meant to undermine the country’s credibility. However, forensic data from Amnesty’s Security Lab casts doubt on these dismissals and suggests there is more to the story.
The Technical Intricacies of Spyware
Once the Predator spyware is activated, it seamlessly integrates into the device’s background processes and starts collecting sensitive information. This form of cyber espionage establishes a communication channel between the compromised device and the perpetrator’s command-and-control server, allowing for remote commands. Consequently, the spyware can regularly upload stolen data to a remote server without alerting the user, making recovery and deactivation particularly challenging.
What You Can Do
Cybersecurity is no longer just for tech companies. Individuals must safeguard their online presence, be cautious of links—even in messages from acquaintances—and invest in reliable cybersecurity tools. Awareness is critical, and staying informed about the latest threats can help protect your personal data.
If you’re looking to fortify your cybersecurity knowledge or need assistance navigating these complex issues, feel free to connect with Pro21st. Together, we can create a safer digital experience.